Introduction
In today’s interconnected world, computer networks form the backbone of our digital infrastructure. They enable the seamless transfer of data and information across vast distances, connecting people and devices like never before. Understanding the fundamental concepts of computer networks is essential for anyone looking to delve into the realm of technology and communication. In this comprehensive guide, we will explore the core principles, components, and protocols that make up computer networks.
Concepts of Computer Networks
A computer network is a interconnected system of computers and devices that communicate and share resources, enabling data exchange and collaboration. These networks can be as small as a home network connecting a few devices or as vast as the global internet.
Computer networks rely on a set of protocols and hardware components to function. Protocols define the rules for data transmission and ensure that devices can understand and interact with each other. Hardware components include routers, switches, and cables that physically connect devices.
Networks serve various purposes, such as sharing files and printers in a local area network (LAN), accessing websites and emails over the internet, or facilitating communication between distant offices in a wide area network (WAN).
They can also be classified by their topology, like star, bus, or mesh, and by their scope, such as LAN, WAN, or the internet. Security is a critical concern in computer networks, with measures like firewalls and encryption used to protect data from unauthorized access.
In summary, computer networks are essential infrastructures that enable the efficient sharing of information and resources among interconnected devices, playing a pivotal role in modern communication and technology-driven societies.
Types of Computer Networks
There are several types of computer networks, each designed to serve specific purposes and accommodate different communication needs. Here are some common types of computer networks.
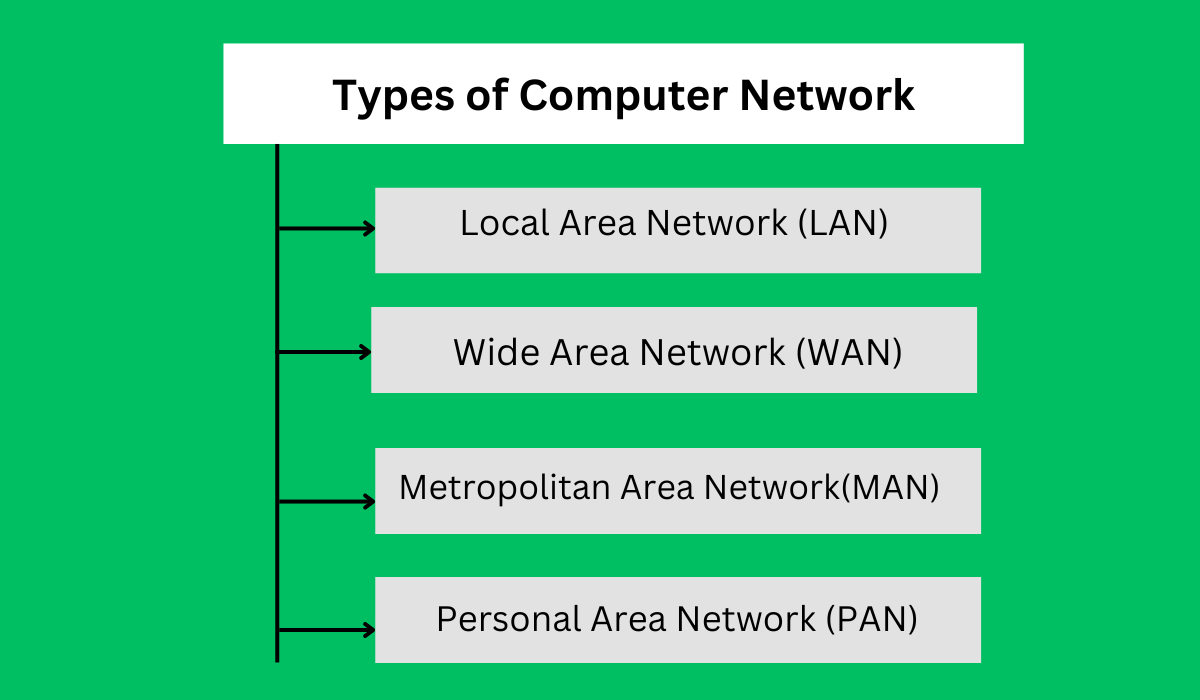
Local Area Network (LAN)
A Local Area Network (LAN) is a network of interconnected devices within a limited geographic area, like a home, office, or school. LANs enable efficient communication and resource sharing among connected computers, printers, and other devices. They typically use Ethernet cables or Wi-Fi to establish connections. LANs are characterized by high data transfer rates, low latency, and relatively low costs.
LANs are often used to share internet access, files, and printers among users in the same vicinity. They are essential for collaborative work environments, allowing seamless data exchange and centralized management of resources. LANs can be simple, such as a home network, or complex, like those found in large corporations. Security measures like firewalls and access controls are vital to protect LANs from unauthorized access or data breaches. Overall, LANs are the backbone of local digital connectivity, facilitating efficient data exchange and cooperation among devices.
Wide Area Network (WAN)

A Wide Area Network (WAN) is a vast communication network that spans over a large geographical area, connecting various local networks or devices. It utilizes technologies like fiber optics, satellite links, or leased lines to enable data transmission between distant locations.
WANs are commonly used by businesses and organizations to interconnect branch offices, data centers, and remote users, facilitating seamless sharing of data, applications, and resources.
They offer scalability and reliability but may involve higher costs and latency due to the extended distance. WANs are crucial for global internet connectivity and support various services, including email, video conferencing, and cloud computing.
Metropolitan Area Network (MAN)
A Metropolitan Area Network (MAN) is a computer network that spans a city or a large campus, connecting multiple local area networks (LANs) within a geographical area. MANs provide high-speed data transfer and communication capabilities for businesses, organizations, and educational institutions in urban or suburban areas.
They typically utilize various technologies such as fiber-optic cables, wireless connections, or a combination of both to enable efficient data exchange over a broad geographic region. MANs are designed to support the connectivity needs of larger communities and facilitate the sharing of resources, data, and services among different entities within the metropolitan area.
Personal Area Network (PAN)
A Personal Area Network (PAN) is a small-scale network that connects devices within a limited physical space, typically within a range of a few meters to a few tens of meters. PANs are designed for personal and local use, facilitating communication between devices like smartphones, laptops, tablets, and peripherals such as keyboards, mice, and headphones.
Bluetooth and Wi-Fi are commonly used technologies for PANs, enabling seamless data transfer, internet access, and device synchronization. PANs enhance convenience and productivity by enabling wireless connections between personal devices, making them essential for modern mobile computing and smart home applications.
Network Topologies
Network topologies refer to the physical or logical layout or structure of a computer network. These topologies define how devices and nodes are connected to one another and how data is transmitted within the network.
Types of Network Topologies
There are several common network topologies, each with its own advantages and disadvantages. Here are some of the most common network topologies:
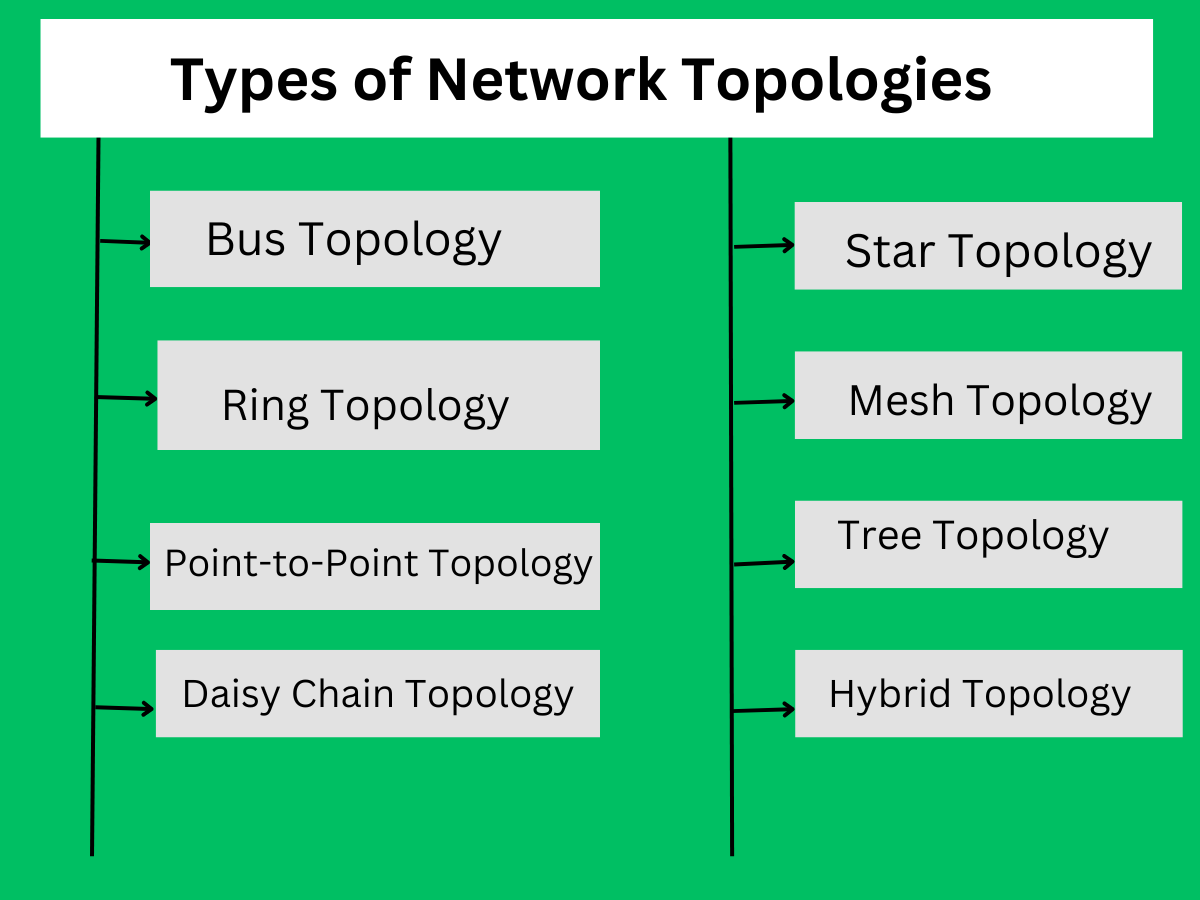
- Bus Topology:
- In a bus topology, all devices are connected to a single central cable called the “bus” or “backbone.”
- Data is transmitted in both directions along the bus.
- It’s simple and inexpensive to set up but can be prone to network disruptions if the main cable fails.
- Star Topology:
- In a star topology, all devices are connected to a central hub or switch.
- Each device has a dedicated connection to the central hub.
- If one device or cable fails, it does not affect the other devices in the network.
- It’s a common choice for Ethernet networks.
- Ring Topology:
- In a ring topology, devices are connected in a circular or ring-like fashion.
- Data travels in one direction around the ring until it reaches its destination.
- It’s relatively fault-tolerant, but a single cable or device failure can disrupt the entire network.
- Mesh Topology:
- In a mesh topology, every device is connected to every other device in the network.
- It provides redundancy and high reliability, as data can take multiple paths.
- It’s commonly used in critical applications like banking and telecommunications.
- Hybrid Topology:
- A hybrid topology is a combination of two or more different topologies.
- For example, a network might have a star topology within each department but use a bus topology to connect the different departments.
- This allows for customization to meet specific needs.
- Tree Topology:
- Tree topology combines characteristics of both star and bus topologies.
- It has a central root node (like a star), with branches and sub-branches (like a tree) connecting devices.
- It’s suitable for larger networks but can be complex to manage.
- Point-to-Point Topology:
- In a point-to-point topology, two devices are directly connected.
- It’s often used for simple connections like serial communication between two computers.
- Daisy Chain Topology:
- In a daisy chain topology, devices are connected in a linear fashion, one after the other.
- It’s simple but can suffer from network disruptions if a device in the chain fails
Network Devices
In computer networks, various devices are used to facilitate communication and the transfer of data between different devices or nodes. These network devices play specific roles in ensuring that data is transmitted efficiently and reliably across the network. Here are some common network devices:
- Router: Routers are key devices in a network that connect different networks together. They determine the best path for data packets to travel between networks, making decisions based on IP addresses. Home routers also provide functions like Network Address Translation (NAT) and firewall capabilities.
- Switch: A switch is used to connect devices within a local area network (LAN). It operates at the data link layer (Layer 2) and uses MAC addresses to forward data packets to the appropriate destination device on the same network.
- Hub: Hubs are older and less intelligent than switches. They simply broadcast data to all devices in a network, which means that all devices connected to a hub receive the data. This can lead to network congestion and reduced efficiency.
- Access Point (AP): Access points are used to provide wireless connectivity in a wired network. They allow wireless devices like laptops and smartphones to connect to a wired network. In many cases, wireless routers have built-in access points.
- Modem: Short for modulator-demodulator, a modem is used to convert digital data from a computer into analog signals for transmission over analog communication lines like telephone lines or cable systems. It also converts incoming analog signals back into digital data for the computer.
- Firewall: Firewalls are security devices that protect a network from unauthorized access and potential threats. They can be implemented in both hardware and software forms and filter incoming and outgoing network traffic based on predefined security rules.
- Load Balancer: Load balancers distribute network traffic across multiple servers or resources to ensure efficient use of resources, minimize response times, and improve the availability and scalability of applications and services.
- Proxy Server: A proxy server acts as an intermediary between a client and a destination server. It can provide security, caching, and content filtering services. Clients send requests to the proxy server, which then forwards them to the destination server and returns the response to the client.
- Gateway: A gateway is a device that connects two different networks that use different protocols. It translates data between the two networks, allowing them to communicate effectively.
- Network Attached Storage (NAS): NAS devices are specialized file storage devices that are connected to a network and provide centralized file storage and access to multiple users and devices.
- Network Printer: Network printers are printers that are directly connected to a network, allowing multiple users to print to them. They are often equipped with network interfaces like Ethernet or Wi-Fi.
- Cable/DSL Modem: These modems are specifically designed to connect to cable or DSL broadband Internet services, providing high-speed Internet access to homes and businesses.
Protocols in Computer Networks
Computer networks rely on various protocols to ensure effective communication and data exchange between devices. These protocols define the rules and conventions that devices on a network must follow to transmit, receive, and manage data. Here are some essential protocols used in computer networks:
- Transmission Control Protocol (TCP): TCP is a connection-oriented protocol that ensures reliable and ordered data delivery between devices. It establishes a connection, breaks data into packets, and reassembles them at the destination while confirming their receipt.
- Internet Protocol (IP): IP is responsible for addressing and routing packets of data so they can travel across networks and reach their intended destinations. IPv4 and IPv6 are the most common versions of IP.
- Hypertext Transfer Protocol (HTTP): HTTP is used for transferring web pages and resources such as images and videos on the World Wide Web. It is the foundation of data communication on the internet.
- Hypertext Transfer Protocol Secure (HTTPS): HTTPS is a secure version of HTTP that uses encryption (typically TLS/SSL) to protect the confidentiality and integrity of data exchanged between a web server and a client.
- File Transfer Protocol (FTP): FTP is used for transferring files between devices on a network. It allows users to upload and download files from remote servers.
- Simple Mail Transfer Protocol (SMTP): SMTP is used for sending outgoing email messages. It’s responsible for routing email messages to their intended recipients’ mail servers.
- Post Office Protocol (POP) and Internet Message Access Protocol (IMAP): These are email retrieval protocols. POP downloads email messages from a server to a local client, while IMAP allows users to access their email messages directly on the server.
- Dynamic Host Configuration Protocol (DHCP): DHCP is used to dynamically assign IP addresses and network configuration settings to devices on a network, simplifying network management.
- Border Gateway Protocol (BGP): BGP is used by routers in the global internet to exchange routing and reachability information. It plays a crucial role in directing traffic between different autonomous systems (ASes).
- Simple Network Management Protocol (SNMP): SNMP is used to manage and monitor network devices and their performance. It allows administrators to gather information and control network equipment remotely.
- Secure Shell (SSH): SSH provides secure remote access and authentication over an insecure network, such as the internet. It’s commonly used for managing network devices and servers securely.
- Internet Control Message Protocol (ICMP): ICMP is used for error reporting and diagnostic functions in IP networks. It includes utilities like ping and traceroute.
12. Future Trends in Networking
Future trends in networking are shaping the way we connect and communicate in an increasingly digital world. Key developments include:
- 5G and Beyond: The rollout of 5G networks is revolutionizing connectivity, offering higher speeds, lower latency, and enhanced capacity. Beyond 5G technologies like 6G are already being explored, promising even faster and more reliable connections.
- Edge Computing: With the growth of IoT devices and data-intensive applications, edge computing is becoming crucial. It enables data processing closer to the source, reducing latency and improving real-time decision-making.
- AI-Driven Networking: Artificial intelligence and machine learning are being integrated into networking to optimize traffic management, security, and network maintenance. AI can predict and mitigate network issues, enhancing overall performance.
- Software-Defined Networking (SDN): SDN continues to evolve, providing centralized control and programmability, making networks more adaptable and easier to manage. Network functions virtualization (NFV) complements SDN by virtualizing network services.
- Security Innovations: As cyber threats grow in sophistication, networking is adapting with advanced security measures like zero-trust architectures and blockchain-based solutions to ensure data protection and privacy.
- IoT Expansion: The Internet of Things is expanding, connecting billions of devices. Networking technologies are evolving to support the massive influx of IoT devices, offering improved scalability and efficiency.
- Quantum Networking: In the long term, quantum networking promises unbreakable encryption and ultra-secure communication. Quantum key distribution (QKD) and quantum teleportation are being researched for secure data transmission.
- Green Networking: Environmental sustainability is a growing concern. Networking is moving towards energy-efficient designs and practices, reducing the carbon footprint of data centers and network infrastructure.
- 5G for Industry 4.0: 5G is instrumental in enabling Industry 4.0, where automation and data exchange in manufacturing are prevalent. It enhances industrial automation, remote monitoring, and robotics.
- Global Connectivity: Initiatives like low Earth orbit (LEO) satellite networks aim to provide global internet access, bridging the digital divide in underserved regions.
13. Conclusion
In conclusion, computer networks are the invisible threads that connect our digital world. Understanding their fundamental concepts is crucial for navigating the complexities of the modern technological landscape. Whether you’re a novice or an IT professional, this knowledge will empower you to harness the power of networks for communication, collaboration, and innovation.
14. FAQs
Q1: What is the role of a router in a computer network?
Ans: A router directs data between devices, manages traffic, assigns IP addresses, and connects networks, enabling communication in a computer network.
Q2: How does encryption enhance network security?
Ans: Encryption protects data by converting it into unreadable text, ensuring confidentiality and preventing unauthorized access, enhancing network security.
Q3: What are the advantages of a star topology?
Ans: Advantages of star topology: Centralized control, easy troubleshooting, scalability, minimal network disruption, and efficient data transfer for connected devices.
Q4: Can you explain the difference between LAN and WAN?
Ans: LAN (Local Area Network) is a small, localized network, while WAN (Wide Area Network) covers larger geographic areas, often connecting LANs.
Q5: What are the implications of 5G on future networks?
Ans: 5G will enable faster speeds, lower latency, and massive IoT connectivity, transforming industries, enabling new applications, and reshaping network infrastructure.